
A Simple But Destructive Email Scam
There is an upsurge of email scams, otherwise known as phishing scam where email conversations are intended to trick victims into making payments into a fraudulent bank account. At DewCIS, we take this opportunity to alert Internet users against ongoing email scammers who manipulate email addresses to deceive the victims into trusting the authenticity of the email and obtain sensitive information.
The scam starts by the fraudsters hijacking an otherwise very genuine email conversation between a supplier say of email address Frankline Njuguna <fnjuguna@tamshi.com> resident in Kenya and a genuine client John Doe <johndoe@shippers.com> resident in Spain for example.
Because scammers are motivated by money, they will lay in wait and only hijack the email conversation when a prospect of payment is real.
At this point, the fraudster will create parallel seemingly similar email addresses as follows; Frankline Njuguna <frjuguna@tamshi.dr> for the supplier and John Doe <johrdoe@shippers.com.dr for the customer.
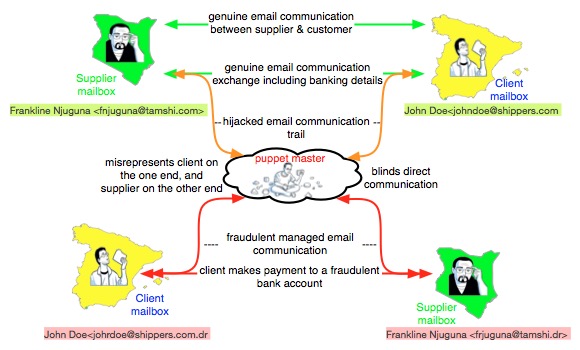
With this communication hijacked, the fraudsters will be well positioned to act as both the supplier and the client sharing only that information they find appropriate such as fraudulent banking details to the unsuspecting client.
The supplier still believing that they are communicating with genuine client negotiates and shares quotations with the client, while the client still believing that they are dealing with the genuine supplier confidently makes payment to the fraudulent bank account. Immediately the money hits their account, the fraudsters immediately cease communication and disappear into thin air.
It is only when the client doesn’t receive the agreed services in time and either makes a call or reach out using another channel to the supplier that the parties realize that they have been defrauded.
This sort of trickery is not very sophisticated at all. The fraudsters are simply taking advantage of our “humanness”; that users do not often care to check the true email addresses of the people they are interacting with. Thus, the fraudsters simply modify the email address but retainsthe username of the source and or recipients, and therefore catching us unawares.
This is very easily done within existing domain registries. For example, it would cost someone just about $ 2 to register a shippers.com.drdomain and create an email address johrdoe@shippers.com.dr for use to defraud unsuspecting users.
From this fraud, it is clear that the fraudsters are possibly collaborating with an insider at either the client or the supplier business; the accomplice who steals the email trail from the mailbox and shares with the fraudsters. Since this is the point of entry and therefore the weakest link, there is need to limit transactional email communications such as those with bank account details to only the necessary staff.
The other very important check is to encourage communication between the customer and the supplier using alternative channels including telephone, WhatsApp etc particularly as a follow-up to ensure the appropriate banking details are shared.
Another practical way of preventing email fraud particularly on sensitive or confidential information is to wrap the content of your emails encrypted with a password that is time bound to expire within a specified time period. To ensure that none other than the intended recipient accesses the message, the passwords ought to be sent via a different channel such as via a phone call or SMS.
While it takes practice to pay attention to domain email addresses of users, we are encourages to always be vigilant so that one can spot the tweaks and tiny differences in email addresses and catch the fraudsters on their tracks and avoid losses.
